Hi, what are you looking for?
Cloud security researcher warns that stolen Microsoft signing key was more powerful and not limited to Outlook.com and Exchange Online.
By
Flipboard
Reddit
Whatsapp
Whatsapp
Email
Researchers at cloud security startup Wiz have an urgent warning for organizations running Microsoft’s M365 platform: That stolen Microsoft security key gave Chinese hackers access to data beyond Exchange Online and Outlook.com.
“Our researchers concluded that the compromised MSA key could have allowed the threat actor to forge access tokens for multiple types of Azure Active Directory applications, including every application that supports personal account authentication, such as SharePoint, Teams, OneDrive,” Wiz researcher Shir Tamari said in a document posted online.
Tamari said the hackers may have also accessed Microsoft customer applications that support the “login with Microsoft” functionality, and multi-tenant applications in certain conditions.
When Microsoft acknowledged the hack and the stolen MSA key, the software giant said Outlook.com and Exchange Online were the only applications known to have been affected via the token forging technique but new research shows that “this incident seems to have a broader scope than originally assumed.”
“Wiz Research has found that the compromised signing key was more powerful than it may have seemed, and was not limited to just those two services,” the company said in a document that provides technical evidence that the stolen MSA key could have been used to forge access tokens Azure Active Directory applications, SharePoint, Microsoft Teams and Microsoft OneDrive.
“Organizations using Microsoft and Azure services should take steps to assess potential impact [beyond email],” Tamari said.
The Wiz research follows news that Chinese hackers were caught forging authentication tokens using a stolen Azure AD enterprise signing key to break into M365 email inboxes. The hack, which led to the theft of email from approximately 25 organizations, turned into a bigger embarrassment when customers complained they had zero visibility to investigate because they were not paying for the high-tier E5/G5 license.
Earlier this week, Microsoft bowed to public pressure and announced it would free up access to cloud security logs and expand logging defaults for lower-tier M365 customers to help with post-incident forensics.
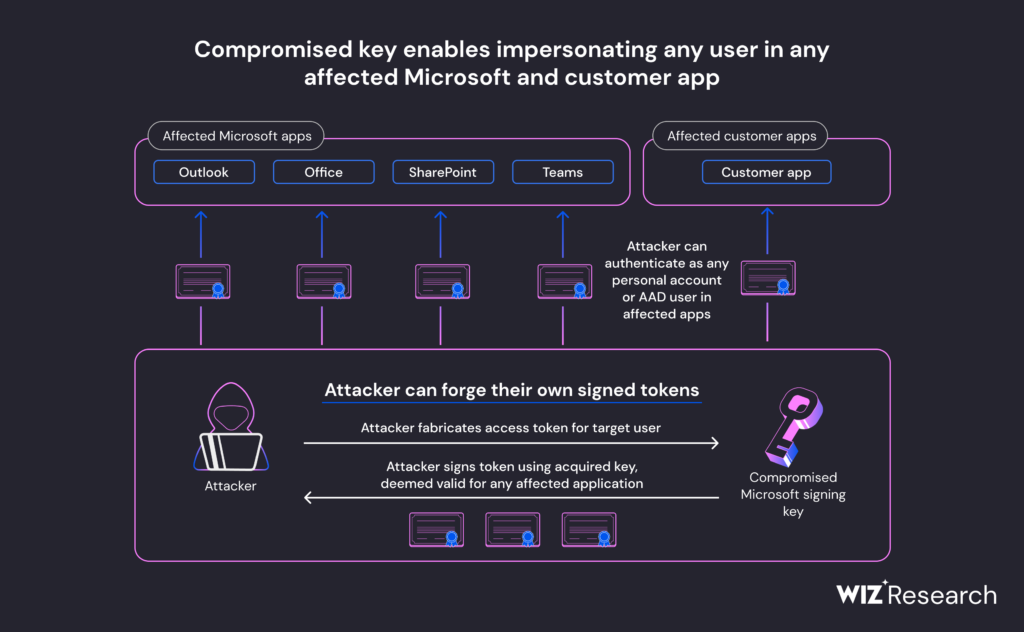
However, Wiz’s Tamari is cautioning that it may be difficult for Redmond’s customers to detect the use of forged tokens against their applications due to lack of logs on crucial fields related to the token verification process.
Although Microsoft has revoked the compromised key, meaning that Azure Active Directory applications will no longer accept forged tokens as valid tokens, Tamari says some problems remain.
“Tokens with extended expiration dates will also be rejected by these applications. However, during previously established sessions with customer applications prior to the revocation, the malicious actor could have leveraged its access to establish persistence. This could have occurred by leveraging the obtained application permissions to issue application-specific access keys or setting up application-specific backdoors,” he added.
“We believe this event will have long lasting implications on our trust in the cloud and the core components that support it,” Wiz said, noting that it’s very difficult to determine the full extent of the incident.
“There were millions of applications that were potentially vulnerable, both Microsoft apps and customer apps, and the majority of them lack the sufficient logs to determine if they were compromised or not,” the company added.
Wiz’s Tamari is recommending that Microsoft customers urgently update Azure SDK deployments to the latest version and ensure application cache is updated to mitigate the risk of a threat actor using the compromised key.
Related: Chinese Cyperspies Use Stolen Microsoft Key to Hack Gov Emails
Related: Microsoft Bows to Pressure to Free Up Cloud Security Logs
Related: Microsoft Warns of Office Zero-Day Attacks, No Patch Available
Related: Microsoft Blames Russian APT for Outlook Zero-Day Exploits
Ryan Naraine is Editor-at-Large at SecurityWeek and host of the popular Security Conversations podcast series. He is a security community engagement expert who has built programs at major global brands, including Intel Corp., Bishop Fox and GReAT. Ryan is a founding-director of the Security Tinkerers non-profit, an advisor to early-stage entrepreneurs, and a regular speaker at security conferences around the world.
Subscribe to the SecurityWeek Email Briefing to stay informed on the latest threats, trends, and technology, along with insightful columns from industry experts.
Join us as we delve into the transformative potential of AI, predictive ChatGPT-like tools and automation to detect and defend against cyberattacks.
As cybersecurity breaches and incidents escalate, the cyber insurance ecosystem is undergoing rapid and transformational change.
![]() More often than not, we are grateful for and celebrate the wrong people. It is incumbent on all of us to take the time to appreciate and acknowledge the doers in our lives. (Joshua Goldfarb)
More often than not, we are grateful for and celebrate the wrong people. It is incumbent on all of us to take the time to appreciate and acknowledge the doers in our lives. (Joshua Goldfarb)
![]() Stepping outside the confines of our comfort zone and embracing a mindset that prioritizes adaptability, shared responsibility, risk-awareness, and preparedness is indispensable in fortifying defenses in the modern distributed network. (Matt Wilson)
Stepping outside the confines of our comfort zone and embracing a mindset that prioritizes adaptability, shared responsibility, risk-awareness, and preparedness is indispensable in fortifying defenses in the modern distributed network. (Matt Wilson)
![]() Organizations need to listen to their CISOs and start turning to cybersecurity automation for the qualitative benefits of employee satisfaction and well-being. (Marc Solomon)
Organizations need to listen to their CISOs and start turning to cybersecurity automation for the qualitative benefits of employee satisfaction and well-being. (Marc Solomon)
![]() AI-powered attacks will become progressively more common, and a well-rounded security approach involves more than simply managing incidents effectively. (Rik Ferguson)
AI-powered attacks will become progressively more common, and a well-rounded security approach involves more than simply managing incidents effectively. (Rik Ferguson)
![]() While applications and cloud infrastructure present different risk profiles and require different security assessments, they must not be viewed separately with regards to enterprise defense. (Tom Eston)
While applications and cloud infrastructure present different risk profiles and require different security assessments, they must not be viewed separately with regards to enterprise defense. (Tom Eston)
Flipboard
Reddit
Whatsapp
Whatsapp
Email
Cycode, a startup that provides solutions for protecting software source code, emerged from stealth mode on Tuesday with $4.6 million in seed funding.
SecurityWeek talks to Billy Spears, CISO at Teradata (a multi-cloud analytics provider), and Lea Kissner, CISO at cloud security firm Lacework.
Okta is blaming the recent hack of its support system on an employee who logged into a personal Google account on a company-managed laptop.
Government agencies in the United States have made progress in the implementation of the DMARC standard in response to a Department of Homeland Security…
Many Fortune 500, FTSE 100 and ASX 100 companies have failed to properly implement the DMARC standard, exposing their customers and partners to phishing…
A CSRF vulnerability in the source control management (SCM) service Kudu could be exploited to achieve remote code execution in multiple Azure services.
Fortinet on Monday issued an emergency patch to cover a severe vulnerability in its FortiOS SSL-VPN product, warning that hackers have already exploited the…
Virtualization technology giant VMware on Tuesday shipped urgent updates to fix a trio of security problems in multiple software products, including a virtual machine…
Got a confidential news tip? We want to hear from you.
Reach a large audience of enterprise cybersecurity professionals
Subscribe to the SecurityWeek Daily Briefing and get the latest content delivered to your inbox.
Copyright © 2023 SecurityWeek ®, a Wired Business Media Publication. All Rights Reserved.
