Hi, what are you looking for?
A SaaS ransomware attack against a company’s Sharepoint Online was done without using a compromised endpoint.
By
Flipboard
Reddit
Whatsapp
Whatsapp
Email
Cybersecurity firm Obsidian has observed a successful ransomware attack against Sharepoint Online (Microsoft 365) via a Microsoft Global SaaS admin account rather than the more usual route of a compromised endpoint.
The attack was analyzed post-compromise when the victim employed the Obsidian product and research team to determine the finer points of the attack. In its blog account of the incident, Obsidian did not disclose the victim, but believes the attacker was the group known as 0mega.
Once in, the attacker created a new Active Directory (AD) user called Omega with elevated privileges, including Global Administrator, SharePoint Administrator, Exchange Administrator, and Teams Administrator; and site collection administrator capabilities to multiple Sharepoint sites and collections. The attacker also removed existing administrators (more than 200) in a 2-hour period.
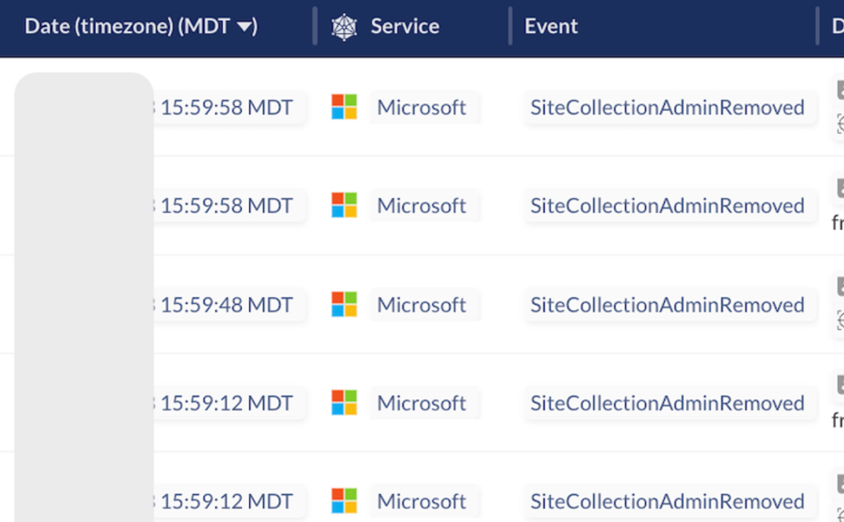
The attack involved only the theft of files rather than theft followed by encryption. After exfiltrating hundreds of files, the attacker then uploaded thousands of PREVENT-LEAKAGE.txt files. These were to alert the victim to the theft and provide a means of communicating with the attacker; that is, to negotiate a payment to avoid having the details published online.
Obsidian suspects this might be the beginning of a trend. “We expect this trend to grow,” the researchers told SecurityWeek. “The attacker invested the time to build automation for this attack, which implies a desire to use this capability in the future. We also suspect it will grow because there are few companies with a strong SaaS security program, whereas many companies are well invested in endpoint security products.”
Relying on data theft alone rather than theft followed by encryption is a growing practice. It avoids the attacker getting a bad reputation through failed decryption routines, and is easier to administer.
Obsidian believes the Omega group (recognizable by the created account name, other observables, and the infrastructure used) was behind the attack. Omega became visible in July 2022 when a report noted it was using double extortion (ransomware plus data theft), and had a leaks site claiming 152 GB of data stolen from an electronics repair company in May 2022.
If Obsidian is correct in pointing the finger at Omega, we may yet learn the identity of the victim through the data leaks site if it refuses to pay the ransom.
The apparently obvious moral to this attack is to use MFA – preferably for all accounts, but most especially for highly privileged accounts. Credentials can be obtained by bad actors from many sources: from their own phishing exercise, by guesswork, from dark web credential databases, or from criminal access brokers. The requirement for MFA makes the use of stolen credentials more difficult – but not, says Obsidian, impossible.
“Even if the administrative account had MFA enabled, the attacker could have obtained or paid for the password on a forum, and then performed MFA push fatigue attacks,” said the researchers. “Ultimately” they added, “companies can further harden their environments against these attacks; for example, by using phishless technologies like WebAuthn.”
“Companies,” concludes the report, “pour hundreds of thousands to millions of dollars into SaaS to enable their business, commonly entrusting regulated, confidential, and otherwise sensitive information to these applications. While meaningful progress has been made on endpoint, network, and cloud threat detection, SaaS threat detection remains an area that many companies are still only beginning to consider.”
It recommends hardening SaaS controls, roping in excessive privileges, and revoking unsanctioned or high risk integrations; together with consolidation and analysis of associated SaaS audit/activity logs to uncover patterns consistent with a breach, an insider threat, or a compromised third-party integration.
Related: Ransomware Group Used MOVEit Exploit to Steal Data From Dozens of Organizations
Related: Western Digital Confirms Ransomware Group Stole Customer Information
Related: Payments Giant NCR Hit by Ransomware
Kevin Townsend is a Senior Contributor at SecurityWeek. He has been writing about high tech issues since before the birth of Microsoft. For the last 15 years he has specialized in information security; and has had many thousands of articles published in dozens of different magazines – from The Times and the Financial Times to current and long-gone computer magazines.
Subscribe to the SecurityWeek Email Briefing to stay informed on the latest threats, trends, and technology, along with insightful columns from industry experts.
Join the session as we discuss the challenges and best practices for cybersecurity leaders managing cloud identities.
SecurityWeek’s Ransomware Resilience and Recovery Summit helps businesses to plan, prepare, and recover from a ransomware incident.
Ex-NSA chief Paul Nakasone has been appointed founding director of the Institute for National Defense and Global Security at Vanderbilt University.
Garo Doudian has joined NextGen Healthcare as Chief Information and Security Officer (CIO/CISO).
Denmark-based cybersecurity solutions firm Heimdal announced the appointment of Jesper Frederiksen as its new CEO.
![]() Organizations need to look beyond preventive measures when it comes to dealing with today’s ransomware threats and invest in ransomware response. (Torsten George)
Organizations need to look beyond preventive measures when it comes to dealing with today’s ransomware threats and invest in ransomware response. (Torsten George)
![]() As cyber threats grow more sophisticated, America cannot afford complacency. The time for decisive action and enhanced cyber resilience is now. (Danelle Au)
As cyber threats grow more sophisticated, America cannot afford complacency. The time for decisive action and enhanced cyber resilience is now. (Danelle Au)
![]() As you look to navigate RSA Conference, with so many vendors, approaches and solutions, how do you know what solutions you should be investing in? (Marc Solomon)
As you look to navigate RSA Conference, with so many vendors, approaches and solutions, how do you know what solutions you should be investing in? (Marc Solomon)
![]() Microsoft provides an easy and logical first step into GenAI for many organizations, but beware of the pitfalls. (Alastair Paterson)
Microsoft provides an easy and logical first step into GenAI for many organizations, but beware of the pitfalls. (Alastair Paterson)
![]() Jennifer Leggio makes the case for more alcohol-free networking events at conferences, and community-building opportunities for sober individuals working in cybersecurity. (Jennifer Leggio)
Jennifer Leggio makes the case for more alcohol-free networking events at conferences, and community-building opportunities for sober individuals working in cybersecurity. (Jennifer Leggio)
Flipboard
Reddit
Whatsapp
Whatsapp
Email
The changing nature of what we still generally call ransomware will continue through 2023, driven by three primary conditions.
Satellite TV giant Dish Network confirmed that a recent outage was the result of a cyberattack and admitted that data was stolen.
Sony shares information on the impact of two recent unrelated hacker attacks carried out by known ransomware groups.
Several major organizations are confirming impact from the latest zero-day exploits hitting Fortra’s GoAnywhere software.
KFC and Taco Bell parent company Yum Brands says personal information was compromised in a January 2023 ransomware attack.
Alphv/BlackCat ransomware group files SEC complaint against MeridianLink over its failure to disclose an alleged data breach caused by the hackers.
Johnson Controls has confirmed being hit by a disruptive cyberattack, with a ransomware group claiming to have stolen 27Tb of information from the company.
Industry professionals comment on the recent disruption of the Hive ransomware operation and its hacking by law enforcement.
Got a confidential news tip? We want to hear from you.
Reach a large audience of enterprise cybersecurity professionals
Subscribe to the SecurityWeek Daily Briefing and get the latest content delivered to your inbox.
Copyright © 2024 SecurityWeek ®, a Wired Business Media Publication. All Rights Reserved.
